2021.12.27 07:54:50 (1475359501016776707) from Daniel J. Bernstein, replying to "Lúcás Meier (@cronokirby)" (1475128624789565449):
You mean examples of being blind to this observation? For various case studies, see the "machinery of cryptographic performance advertising" subsections inside https://cr.yp.to/papers.html#competitions. For the incentive structures naturally driving this phenomenon, see Section 3.8 of that paper.
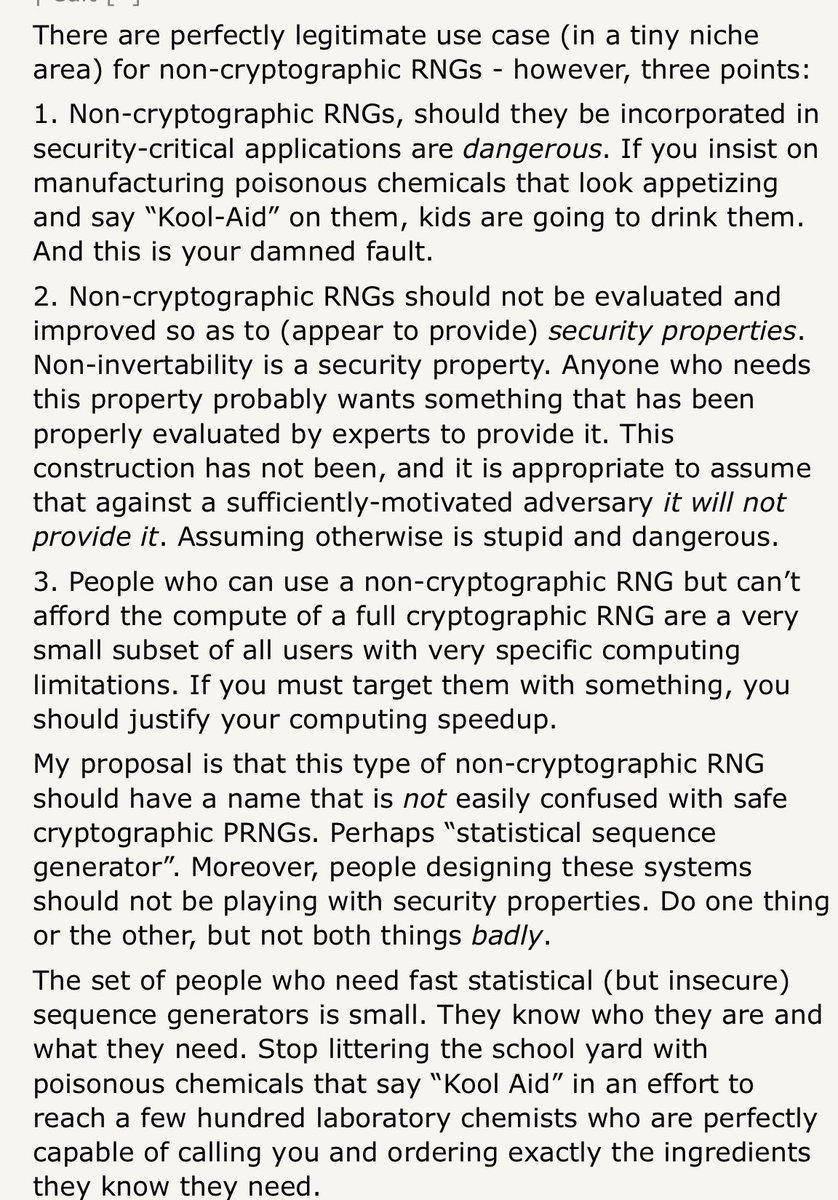
2021.12.21 00:45:15 (1473077063678582787) from "Matthew Green (@matthew_d_green)", replying to "Matthew Green (@matthew_d_green)" (1473069816273588229):
I want to live in a world where “random number generator” and “pseudorandom number generator” refer to secure things. And there is this other class of things like “statistical sequence generator” that others can play with and make fast.
2021.12.21 01:11:44 (1473083729505570821) from "Matthew Green (@matthew_d_green)", replying to "Matthew Green (@matthew_d_green)" (1473077063678582787):
Ok I wrote down all my thoughts and will shut up now.
2021.12.26 16:34:02 (1475127773497020420) from Daniel J. Bernstein:
It's impressive how clearly we cryptographers can see and communicate that strong cryptography is fast enough for basically everybody when this observation threatens research in other areas, and how blind we can be to the same observation when it threatens cryptographic research. https://twitter.com/matthew_d_green/status/1473083729505570821
2021.12.26 16:37:25 (1475128624789565449) from "Lúcás Meier (@cronokirby)":
For example?