2018.05.01 07:49:05 (991192767148806144) from Daniel J. Bernstein, replying to "Luca De Feo (@luca_defeo)" (991126180546924544):
Running to the max on each exponent sounds like an easy way to be constant-time, at the expense of a 2x slowdown. Atomic blocks would be faster and would leak only the total length of the computation, which could be chosen to be constant.
2018.05.01 01:03:21 (991090658260766722) from "Luca De Feo (@luca_defeo)", replying to "Deirdre Connolly¹ (@durumcrustulum)" (991090103689908224):
That's a matter of nomenclature, but I wouldn't call that a "key validation". FO validates a key pair, not a public key.
2018.05.01 01:08:42 (991092005756461056) from "Luca De Feo (@luca_defeo)", replying to "Luca De Feo (@luca_defeo)" (991090658260766722):
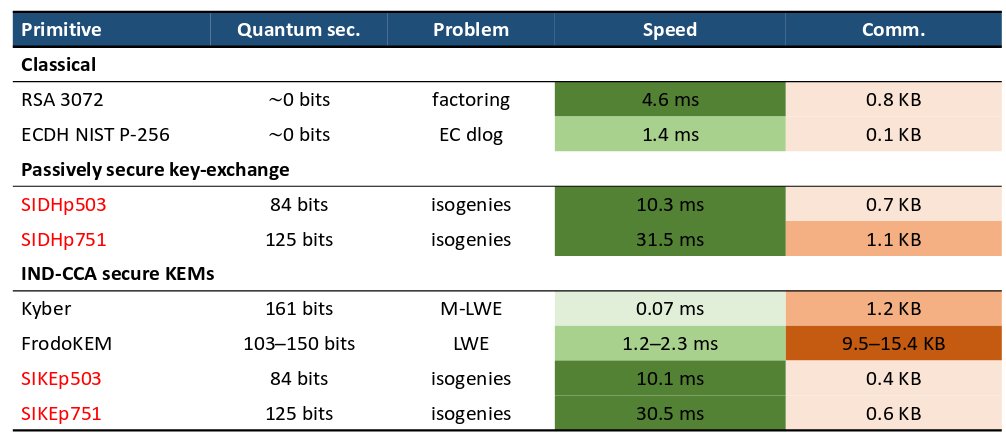
Anyway, if your question is about SIKE vs Hashed El Gamal from CSIDH, SIKE is about as efficient as SIDH: https://rwc.iacr.org/2018/Slides/Longa.pdf
2018.05.01 03:10:21 (991122620538994694) from "Patrick Longa (@PatrickLonga)", replying to "Luca De Feo (@luca_defeo)" (991092005756461056):
Note that more work is still needed to claim that CSIDH is practical. Although promising, this first implementation is only a proof-of-concept and not ready for real-world use. More specifically, it doesn't run in constant-time.
2018.05.01 03:24:30 (991126180546924544) from "Luca De Feo (@luca_defeo)", replying to "Patrick Longa (@PatrickLonga)" (991122620538994694):
I have the feeling we have a volunteer :)